Note: This is a port of my twitter thread
At the end of October 2019, WhatsApp (owned by Facebook) sued NSO. The complaint covered multiple different legal attacks (including a reference to the CFAA) but the technical exhibits consolidated a lot of public technical information on NSO that I thought was worth digging into.
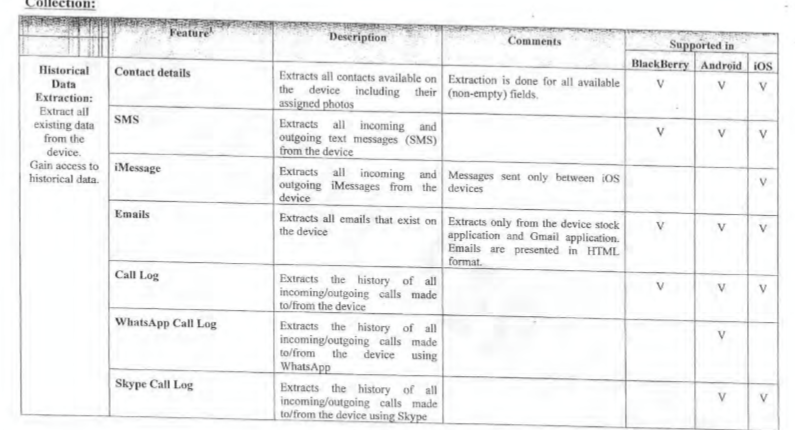
Two exhibits - a user manual and a contract with Ghana - reveal quite a bit on NSOs system design and thinking. Unless labeled otherwise, screenshots are from the user manual and not the contract.
First off, the user manual describes the different attack methods available in Pegasus, NSO’s primary tool. The user manual mentions multiple attack methods such as over the air zero click, phishing messages, attacks over GSM abusing fake BTS (Base Transceiver Station) and physical attacks using data cables.

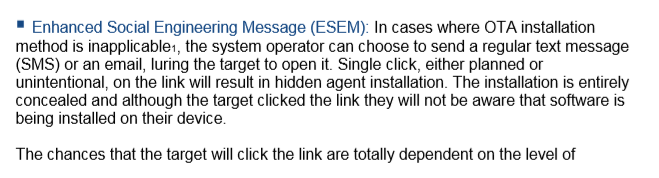

A common problem when attacking Android devices is device fragmentation. For many remote exploits, the attackers will have to customize the exploit for each platform. Also, every Android phone has its own quirks and bugs the developers have to work around.


At the time, NSO specified up to 8 weeks to handle new target devices. I have a hard time believing this is the required timeframe, it’s likely a large buffer for HR reasons or because it takes time to acquire phones.
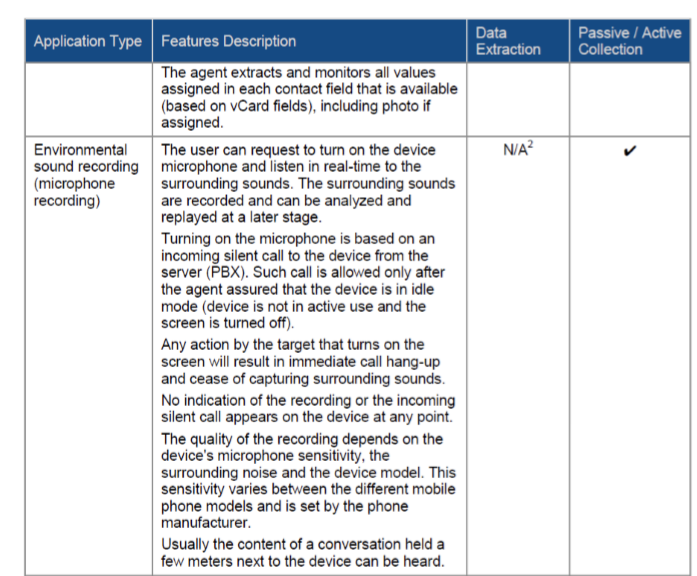
The tool itself has a laundry list of features. Like other mobile malware, Pegasus can silently activate the user’s microphone to listen in to passive communication.
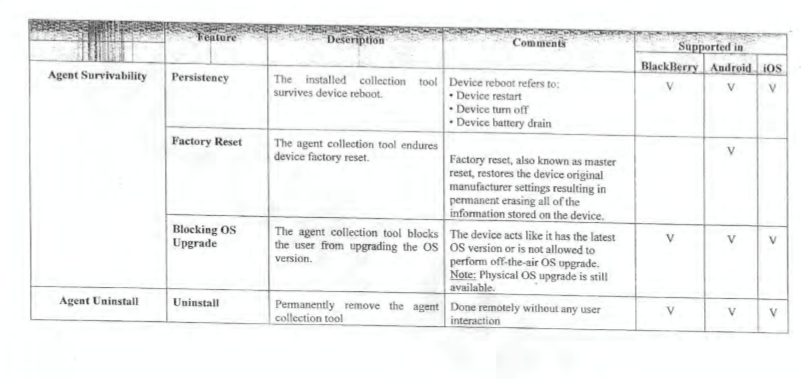
Let’s skip ahead to the contract, which also contains technical information. Looking at the contract, at the time of this document, NSO did not know how to make their malware survive factory resets on iPhone, nor extract WhatsApp data from iPhones.
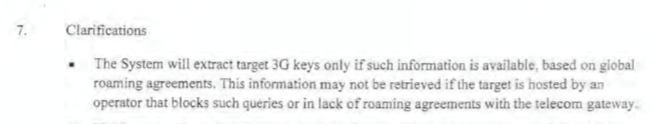
Last, their cellular (SS7) capabilities deserve their own thread by experts. Their SS7 capability list reads like they explicitly allow for cases where control messages are sent across operator networks.
A serious problem for any mobile malware is sending the information home when a network connection is not available. Also, unlike PC malware, the phone’s battery life is very sensitive to network communication, as is the user’s phone bill (for some countries).
What Pegasus does is typical, it buffers information until the phone is near a rapid network, such as Wifi. If the buffer fills up before that time, the malware will override old data.

Every good operator needs a way to hide communication traces. It’s not clear how many hops NSO feels are required but probably more than one.

Also, according to the contract, the client is responsible for their own operational security. The target may notice if the spying software ends up in their billing record.

I’m curious if NSO cares about android antivirus or they simply think to themselves: “whatever, they all suck”.

The difference between most malware and commercial offerings is typically the UI and backend. NSOs user manual shows that it offers more than just a typical RAT control panel but also many sophisticated intelligence queries such as geo-fencing alerts and alerts on targets meeting up with each other.

Like other enterprise software, NSO provides an installation manual. I’m not surprised NSO specifies every last bit of their install process. Because as is common in the enterprise world, what isn’t defined is left up to chance. I’m sure they have customers who would try to cheap out on internet access and have no redundancy, or run the servers somewhere with bad electrical routing - leaving themselves open to sily failures that may expose them to their targets.
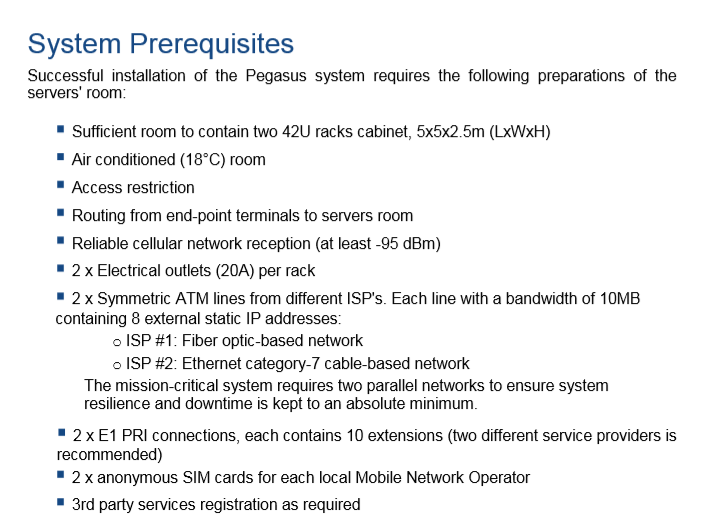
These requirements also extend to Opsec. Reading the contract, governments are encouraged to hide their tracks even when spying inside their own nation.

Moving on to the contract, NSO seems to be prepared for the Israeli Ministry of Defence unilaterally removing their export license.

Along with technical restrictions on what countries you are allowed to target.

I noted I would focus on technical information, but at the end, I should just mention - 25 devices at 8 million dollars feels like a steal.


In this case, we see the contract specifies a total of 25 concurrent implants. From other sources, NSO supports two methods of operation. One, as specified in this contract, allows for X number of concurrent malware implants. Another is a magazine metaphor, you are provided with N attacks you can use as you wish.
References: